Aleksey Lapshin Discusses the Power of ANY.RUN’s Interactive Platform In Our Exclusive Interview
ANY.RUN, founded by Aleksey Lapshin, is an advanced online malware analysis platform that enables real-time, interactive research for cybersecurity professionals. It allows users to actively control sandbox simulations and analyze suspicious files with dynamic and static capabilities, offering deeper insights into malware behavior.
The platform’s cloud-based design simplifies analysis with an intuitive interface, reducing equipment costs and making it accessible from any device. ANY.RUN also features a continuously updated malware database, supporting both public research and private threat hunting, making it an essential tool for enhancing cybersecurity efforts globally.
We sat down with the company’s founder, Aleksey Lapshin, to learn more about the World Future Awards-winning firm.
World Future Awards: What inspired you to create ANY.RUN, and how did you identify the need for a more interactive and real-time malware analysis platform?
Aleksey Lapshin: Back when I was a malware analyst, I saw my colleagues having a tough time with the tools they used in their work. The providers of these solutions prioritized business goals over the professionals’ actual needs. This motivated me to take a different path.
The product’s concept was driven by several problems I encountered as a malware analyst. The automated solutions I used provided minimal information about the sample, without allowing me to dig deeper, observe the malware execution process, and make my decision about the threat. The alternative was to use my own virtual machine but setting it up was time-consuming and required frequent adjustments.
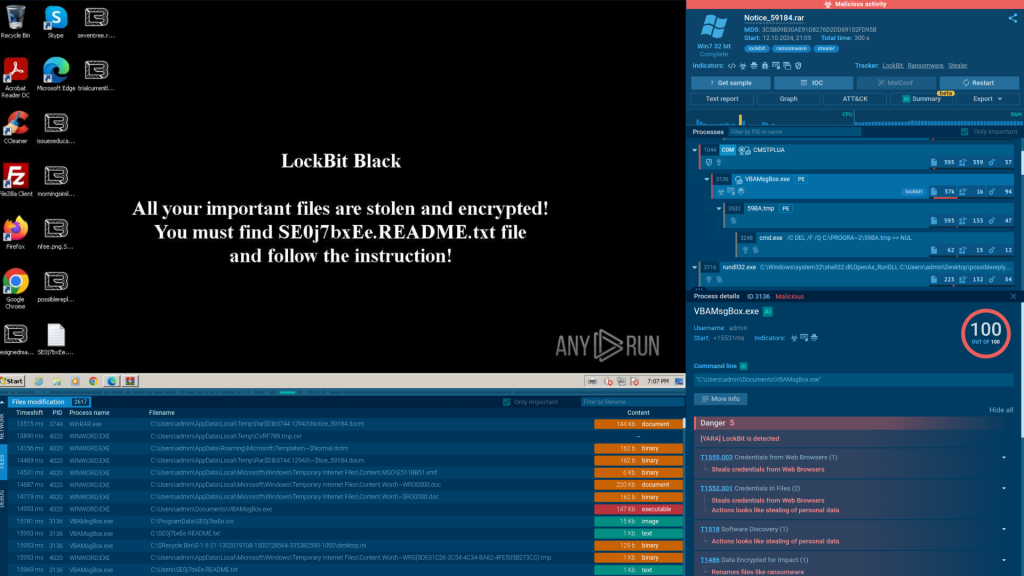
This led me to the idea of creating a sandbox that would combine real-time interactivity and control over the analysis process with a detailed view of malicious activities, all within a user-friendly interface. And that’s how ANY.RUN was born.
WFA: ANY.RUN’s interactive nature is one of its key differentiators. Can you explain how this interactivity enhances malware analysis compared to traditional automated tools?
AL: Unlike automated solutions, which limit your ability to engage with the sample and instead rely on their built-in mechanisms to force execution, ANY.RUN gives you control over the analysis process. You can interact with malware and phishing threats in real-time, seeing how they respond to your inputs.
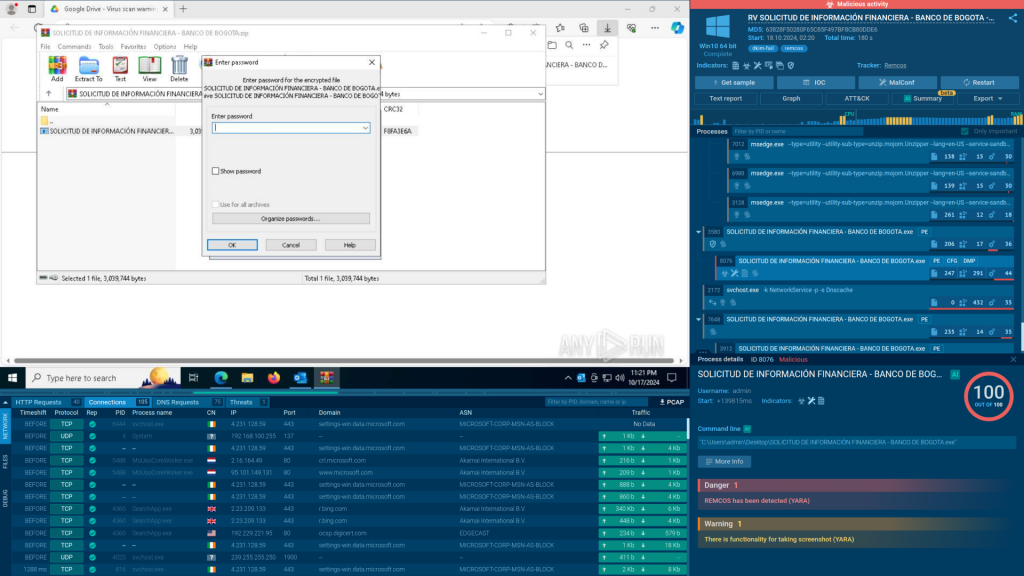
This is especially useful for multi-stage attacks, as you can safely follow the entire kill chain — from a phishing email to downloading and running the payload. This hands-on approach provides deeper insights and helps you respond more effectively to complex threats.
WFA: The platform is designed for users of all skill levels, from beginners to experienced cybersecurity professionals. What were some of the challenges you faced in creating an intuitive interface that meets the needs of such a diverse audience?
AL: The interface ANY.RUN has today comes from lots of trial and error since our early days. One of the biggest challenges was deciding what information to show first and what to keep in the background.
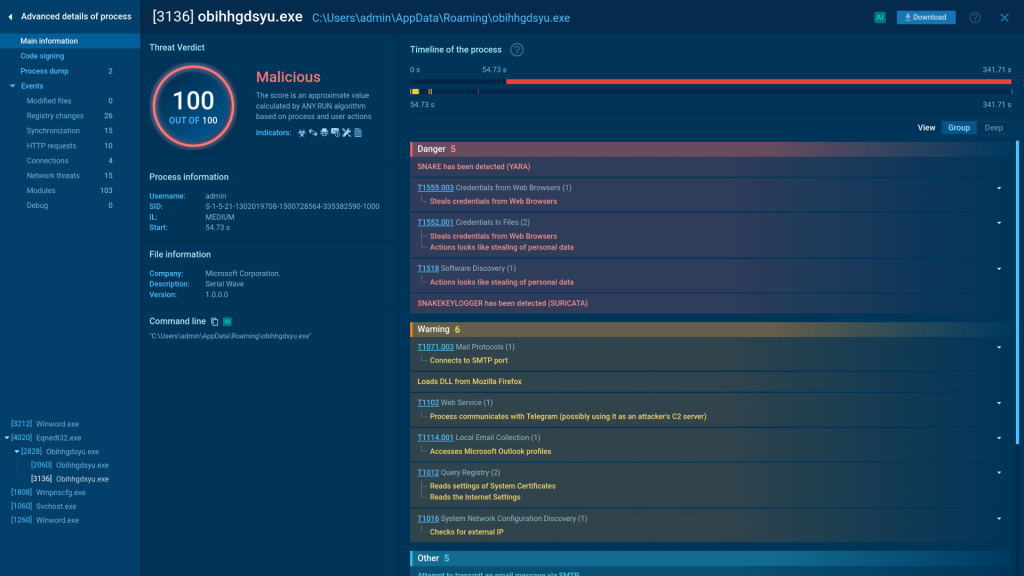
The result is an organized interface with main sections, each focusing on a specific part of the analysis: processes, network traffic, files, etc. To help the user quickly understand what threat they are dealing with, the sandbox displays tags that link the sample to a specific threat or malware family.
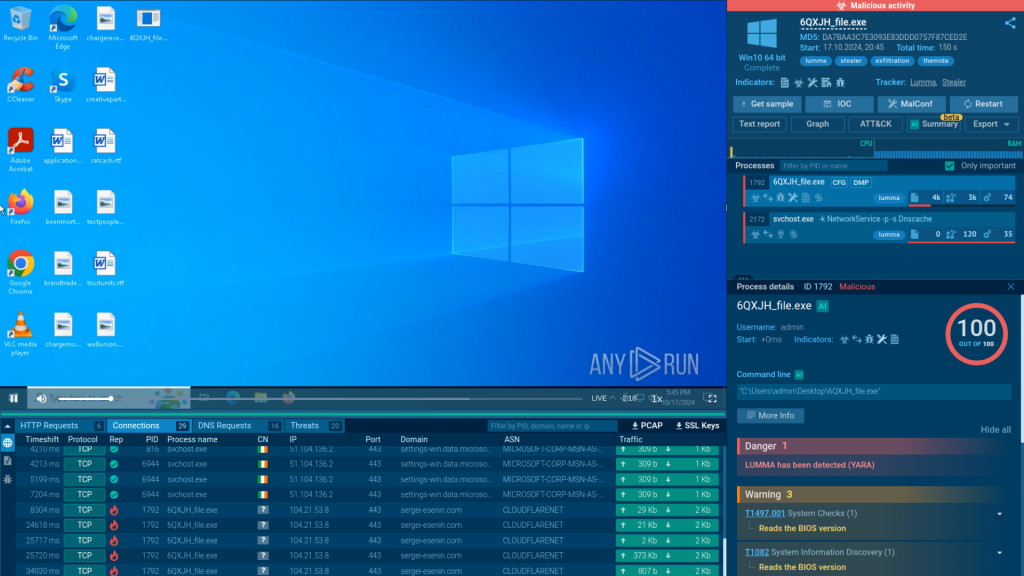
For a deeper look, you can always navigate to the items of your interest to learn more. Whether you want to study traffic for a particular connection, access the Suricata rule used for threat detection, or examine malicious script execution, the sandbox lets you access this info with ease. To highlight important details, we use special indicators.
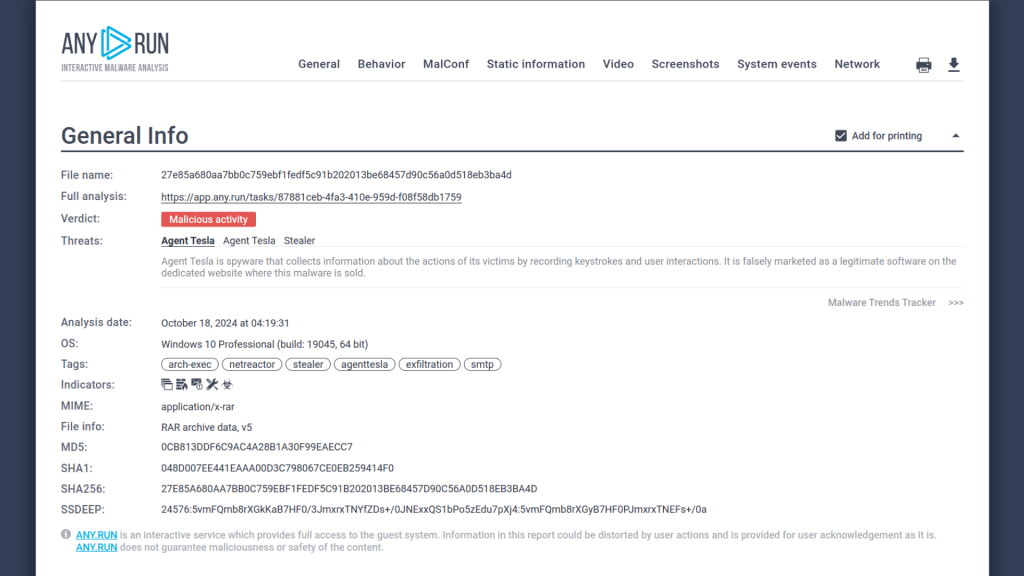
The IOC and Report buttons are also easy to find, making it simple to download and share the collected information.
WFA: Cyber threats are constantly evolving. How does ANY.RUN stay up to date with the latest malware trends, and how is your platform adapting to these new threats?
AL: At ANY.RUN, our Public Submissions page lists all publicly available reports on threats submitted by our global community of over 500,000 users. This helps our analysts stay updated on the current threat landscape and improve our sandbox’s detection capabilities by writing YARA and Suricata rules, as well as adding signatures for various malicious activities.
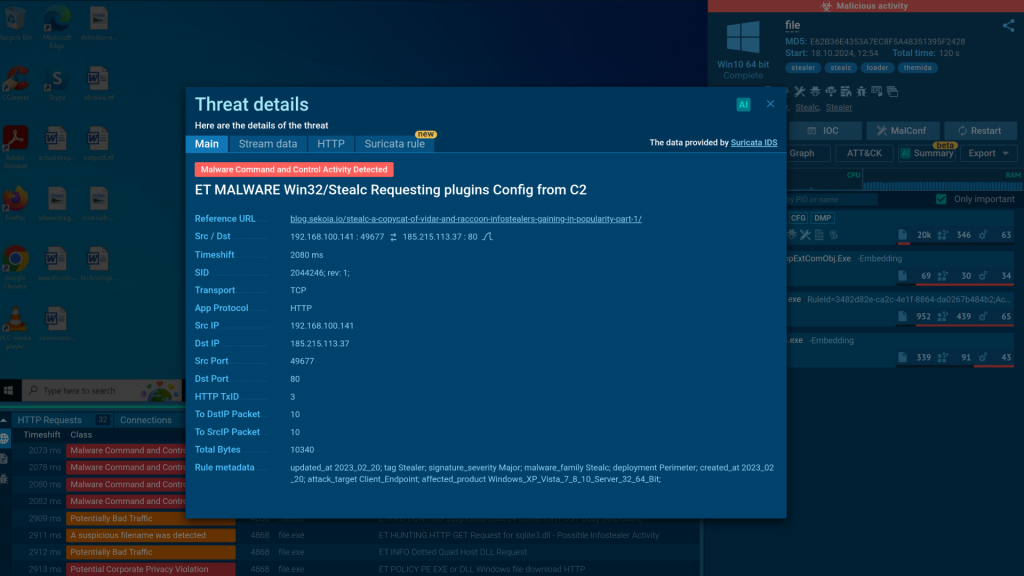
Beyond detecting new threats, we regularly add features to enhance users’ analysis abilities. This year we introduced a Linux sandbox environment to help analysts investigate threats targeting the growing number of Linux servers and endpoints.
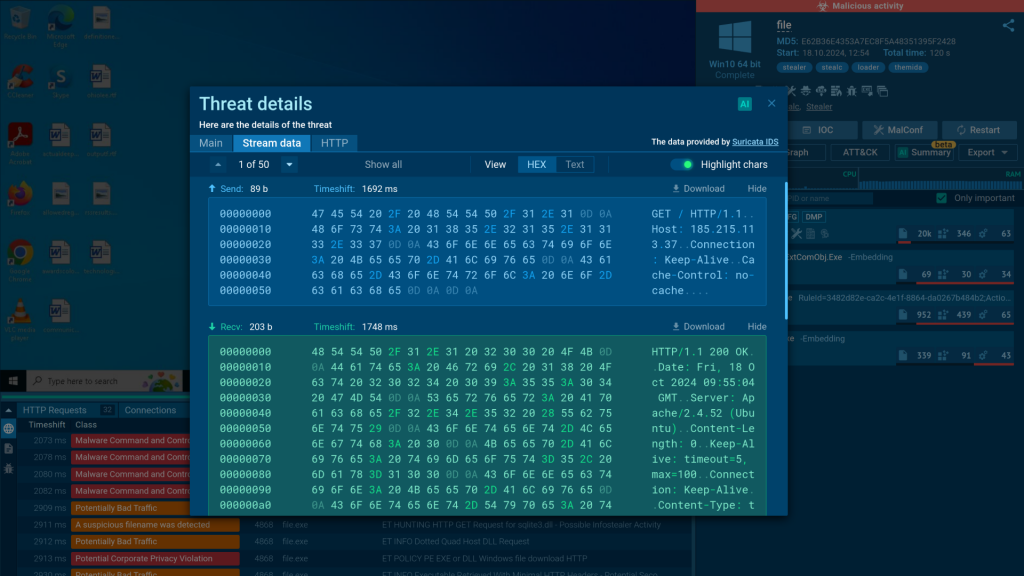
Thanks to our team’s flexibility, we can adapt to new trends fast. Just to give you an example, last year, we spotted a rise in QR code abuse for malware delivery and quickly added a QR code link extractor to our sandbox, making it easier to analyze such attacks.
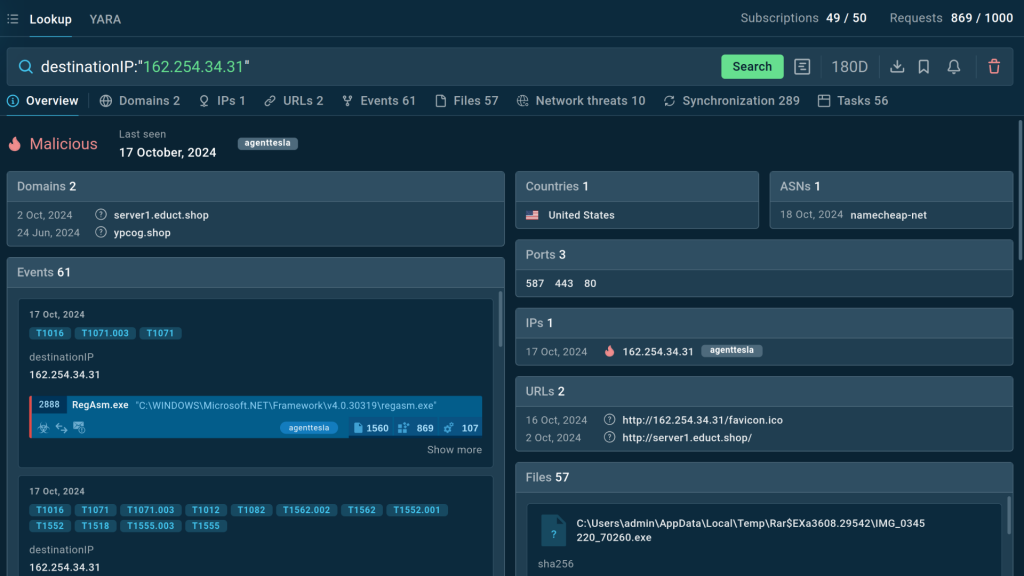
Yet, most importantly, we not only keep up with the trends ourselves, but also help our users stay updated on the latest malware and phishing attacks thanks with ANY.RUN’s Threat Intelligence products: TI Lookup and TI Feeds.
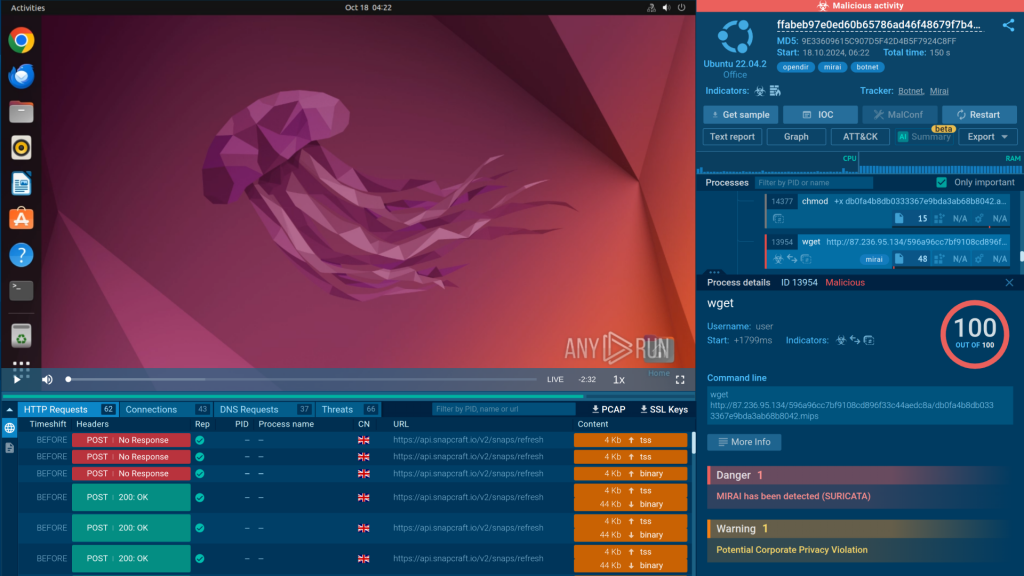
For instance, TI Lookup lets you search our threat database using over 40 parameters, like IP addresses, system events, file names and hashes, registry keys, and even YARA rules, to identify emerging and persistent threats, gather context, and explore related sandbox sessions.
WFA: ANY.RUN offers real-time insights and results within minutes. How does this speed benefit cybersecurity professionals in their daily work, especially when dealing with complex or time-sensitive threats?
AL: This allows security teams to run analyses quickly and accurately with ANY.RUN. You can submit a file and get a report in as little as 40 seconds. Such performance is a great advantage for security teams working under time pressure, when resolving an incident or responding to a cyber attack.
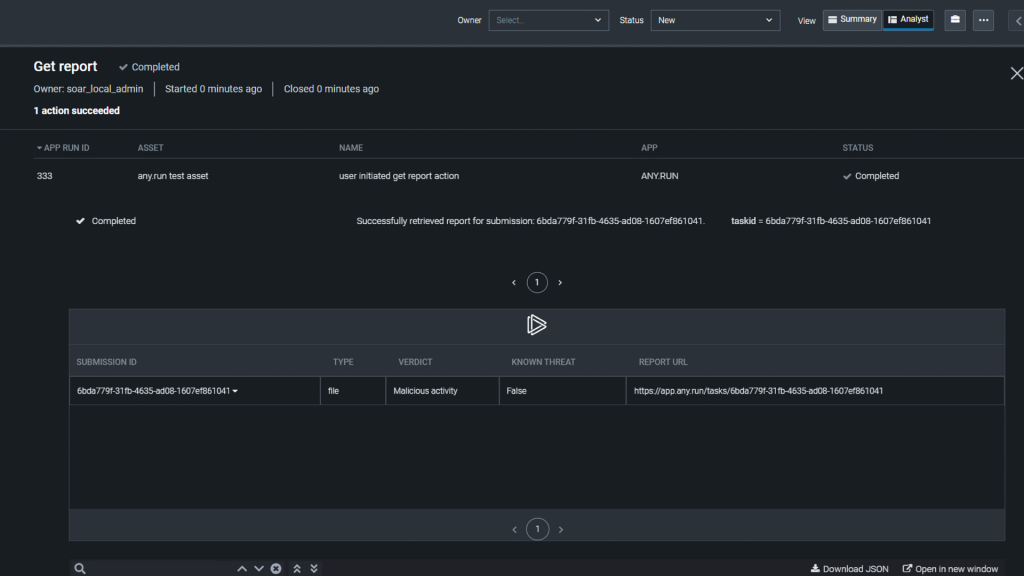
The speed of the sandbox is also great for analysts handling many samples daily. We offer API access for automatic submissions and integrations with Splunk and OpenCTI to help clients keep their operations efficient.
Interactivity plays a huge role here too, saving time on steps that are usually required when using automated sandboxes. Instead of downloading a payload from a file-sharing site on your own machine and then submitting it for analysis, you can do it directly within the ANY.RUN sandbox.
However, sometimes a longer investigation is needed. For this, users can extend the analysis in our VMs to up to 24 minutes to thoroughly examine every aspect of the threat without rushing.
WFA: With the rise of sophisticated malware that can evade detection, what unique features or capabilities does ANY.RUN offer to help researchers and analysts uncover hidden threats?
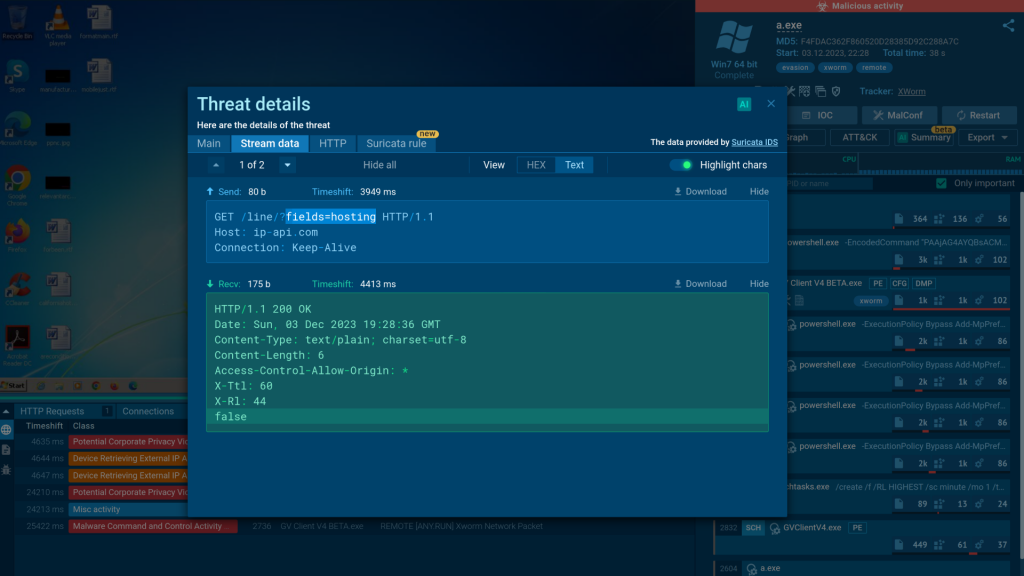
AL: We’re always on the lookout for new evasion techniques to ensure our sandbox can counter them effectively. One key anti-evasion feature in the ANY.RUN sandbox is Residential Proxy. Many malware and phishing threats check where the user’s traffic is coming from. If they detect it’s from a hosting service, they might stop the malware execution or redirect users to a safe site.
The Residential Proxy feature lets you use regular residential IP addresses from dozens of countries. This helps you bypass such checks and force the malware to run. It’s also great for dealing with attacks that target specific regions.
WFA: How does ANY.RUN’s cloud-based infrastructure contribute to the platform’s accessibility and scalability, and how do you see this influencing the future of malware analysis tools?
AL: Thanks to being cloud-based, ANY.RUN can be accessed from anywhere at any time. This makes it easy for users to perform malware analysis without needing specialized hardware or complex setups. This accessibility is especially helpful for remote teams and individuals who need to work on the go.
In terms of scalability, our cloud infrastructure lets us easily adjust resources based on demand. This means we can handle a large number of analyses at once without sacrificing performance. It also allows our clients to scale their teams without investing in additional hardware or infrastructure. They can quickly onboard new analysts and expand their capabilities.
As for the future, I believe that cloud-based cybersecurity solutions will continue to gain popularity. Their flexibility, cost-efficiency, and global accessibility are unmatched.
WFA: Looking ahead, what future developments or features do you envision for ANY.RUN to further empower cybersecurity teams in their fight against cyber threats?
AL: At ANY.RUN, we have a detailed roadmap of new products, features, and updates that we’re closely following. One of our most significant recent releases is Safebrowsing, a service that allows you to quickly open and explore suspicious URLs in an isolated virtual browser, notifying you of any threats.
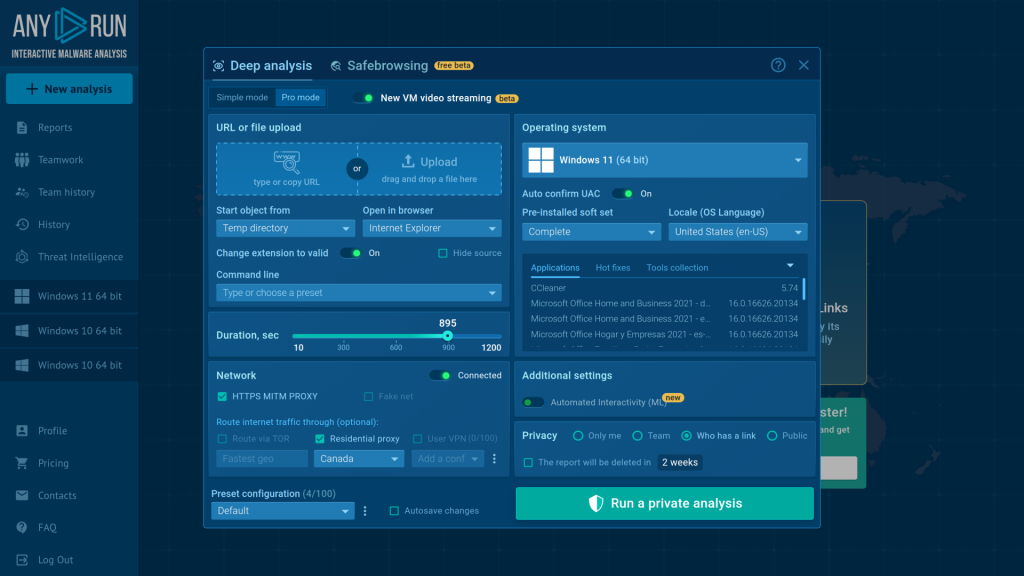
As for future updates, you can expect even more exciting news for the wider cybersecurity community. Make sure to stay tuned for our latest updates on ANY.RUN’s social media and blog.
MORE NEWS

World Future Awards Opens Nominations for 2025 TOP 100 Blockchain and Web3 Companies

Simple Life App: Empowering Sustainable Wellness Through Empathetic and Proactive AI

AI for Good Health: How Simple Life App Is Transforming Weight Loss

World Future Awards Celebrates the Top 100 AI Tech Companies of 2025

Speexx: A Global Pioneer in AI-Powered People Development

Speexx Named One of the Top 100 AI Tech Companies by World Future Awards 2025

Lydia Teryoshina Appointed to World Future Awards Board of Experts
NEWSLETTER
Sign up to learn more about our project and to stay up to date.

